Summary of Storm-0324, According to Microsoft
Storm-0324, also known as DEV-0324, TA543, or Sagrid, is a financially motivated cybercriminal group specializing in initial access to corporate networks. Their modus operandi primarily involves phishing schemes sent via email that lead to the delivery of various malware payloads, including but not limited to banking trojans and ransomware. Importantly, Storm-0324 acts as a gateway for other threat actors, handing off access to compromised networks for further exploitation, such as ransomware attacks.
Starting in July 2023, this group evolved its tactics to exploit Microsoft Teams as a channel for phishing attacks. Storm-0324’s methods are distinct from similar social engineering campaigns like those of Midnight Blizzard (Russian hacking group). Storm-0324’s new approach uses an open-source tool called TeamsPhisher to send malicious links through Teams chats, leveraging a vulnerability first highlighted by the London-based cybersecurity company JUMPSEC.
The group’s operations are highly elusive. They use advanced traffic distribution systems like BlackTDS and Keitaro to avoid detection. Their payloads frequently include JSSLoader malware, which paves the way for another cybercrime group, Sangria Tempest, to conduct ransomware attacks.
Microsoft has taken several measures to mitigate the risks, including suspending compromised accounts and implementing various security enhancements.
The Continuous Threat Loop: How Storm-0324 and Sangria Tempest Use JSSLoader in Their Email-Based Attack Chain
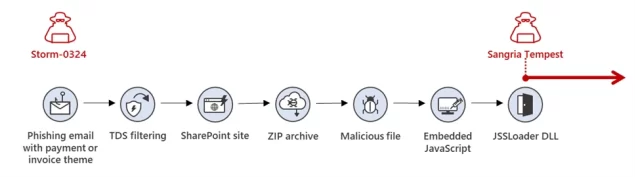
Since 2019, Storm-0324 has been acting as a gateway criminal, handing over initial access to the cybercrime group Sangria Tempest. Their go-to method involves crafting deceptive emails about invoices or payments, which direct users to a SharePoint site that hosts a ZIP file filled with malware. Microsoft is on it—constantly monitoring for abuse across its platforms, taking down harmful activities, and bolstering security measures to make life difficult for these bad actors.
Assessment and Proactive Guidance
Let’s cut through the technical jargon: Storm-0324 is an enabler in the world of cybercrime. They’re the ones who jimmy the window for other criminals to crawl through. Initially, they stuck to email-based attacks but have since upgraded to targeting your Microsoft Teams chats. Yes, the same Teams you use for daily meetings and office banter. It’s like a burglar using your doggie door instead of a crowbar on the window.
So, what should you do about it? First, awareness is vital. Knowing Teams chats can be a vector for phishing attacks is the first step toward vigilance. Ensure your organization’s employees are trained to recognize and report phishing attempts via email and Teams messages.
Next, consider adopting Microsoft’s recommendations: Use Microsoft 365 Defender to detect Storm-0324’s activities and employ the ‘least privilege’ principle for account permissions. That means only giving employees what they need. If Storm-0324 can’t get their foot in the door, there’s less chance of them inviting their nefarious friends to the party.
You’re probably thinking, “Well, isn’t Microsoft doing something about this?” Absolutely. They’ve suspended suspicious accounts and are rolling out security enhancements. But cybersecurity is a team sport. The best offense is a multi-layered defense.
So, keep your software updated and diversify your security strategies. Let’s even go so far as to implement geo-IP filtering to block traffic from high-risk regions. This won’t make you invincible, but it will make you a more challenging target. And often in cybersecurity, that’s enough to make the bad guys look elsewhere.
Be vigilant, be informed, and don’t let Storm-0324—or any other cybercriminal—turn your MSTeams space into their playground.
Source: Microsoft Threat Intelligence | September 12, 2023 | https://www.microsoft.com/en-us/security/blog/2023/09/12/malware-distributor-storm-0324-facilitates-ransomware-access/
